FREEPORTS: The challenge of cyber security
Freeports will be enclaves – at least from a tax perspective – that are digitally interconnected with the ‘outside world’ and this exposes them to a range of cyber threats: from low-level security issues to full-blown geopolitical campaigns. So as the UK gets set to welcome eight Freeports as local and national innovation ecosystems and hotbeds for innovation, their need for resilient digital systems must be a priority, says John Connolly, Head of Security Architecture and Assurance Consulting at Atkins.
The government’s Freeports Bidding Prospectus (published November 2020) states that it wants Freeports to: “unleash the deep potential of our port regions to help create the next generation of jobs, prosperity and opportunity for this country…” While much consideration is currently being given to the physical security of Freeports, such as goods moving across multiple sites within their boundaries for customs, auditing and taxation purposes, or the height of security fences, these factors are only a small part of the overall security landscape we should now be looking at.
A big opportunity for the UK’s cyber security expertise
In the March 2021 Budget announcement, Rishi Sunak announced the location of eight Freeport sites. The coming of the UK’s Freeports give us good reason to be more ambitious when it comes to cyber resilience. This is an opportunity for the UK to set itself apart as a world-leader in secure, intelligent borders – demonstrated by how we will protect our Freeport operations from the playbooks of would-be attackers.
Last year, the Government launched its 2025 UK Border Strategy Public Consultation, to gather the views and expertise of stakeholders in order to form a robust and clear pathway “for delivering the world’s most effective border by 2025”. I believe that a rethink of the UK’s borders also provides a once in a generation chance to develop and deliver world-leading border processes, and I hope the sentiment was echoed by others who contributed to the consultation. The processes that are created must have the power to underpin seamless, data-driven entry and exit to the UK for legitimate goods and people and embrace the challenge of digital transformation. This, I believe, is absolutely key to their success.
Borders beyond the physical realm
This border strategy should also help to develop our current concept of borders beyond the purely physical realm towards a ‘system of systems’ that recognises digital and physical interdependencies at the border. Freeports present the perfect model by which we can deliver on this concept; they are faced with many challenges when it comes to data sharing.
Ambitions may be high, and benefits significant, but so are the risks. Imagine all the means and ways that data can be shared for the benefit of the greater good: in harnessing the strategic trends of big data for port logistics, autonomous Ro-Ro shipping, biosecurity technologies tracking the movement of people, and the visual data capture of vehicles entering or leaving a Freeport.
Making it safe to share
There will be a great appetite and need to share data – but alongside that, an inevitable nervousness of collaboration with the potential for cyber criminality or loss of intellectual property rights, where the overall network will only be as strong as its weakest link. So, this is the time for consortia to think about the practical steps they need to start taking to ensure their cyber resilience is a priority, as Freeports will be treated as key national infrastructure.
It’s time for consortia to ask: what will be their cyber resilient vision? What kind of data will they need to share and protect? What common language will they use? What skills will they need to reach their objectives? Because regulations will apply, and Freeports – which will operate locally, contribute nationally, but are exposed globally – will have to make regular submissions to the Government on National Information Security Standards.
All parties involved in sharing data within a Freeport boundary will inevitably need to be connected to the internet, and most are likely to use or consider migrating to cloud-based information technology (IT) services.
The risks to the confidentiality, integrity and availability of data could have a devastating impact on the organisation: on reputation, on financial consequences, either directly or indirectly, and by creating disrupted operations; even public safety and environmental incidents.
Potential sources of risk:
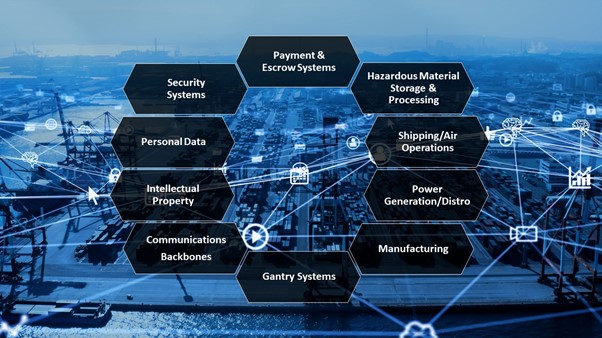
The need for a common standard
Having lots of disparate new and legacy digital systems in operation also gives the opportunity for hardware not to be patched or managed consistently or configured correctly. This means every stakeholder operating within the Freeport is even more exposed in cyberspace to a variety of threats – with its perilous traps such as phishing, water-holing and ransomware. This means even at the most basic level, a common standard must be introduced. At present, the different modes of roads, rail, sea and air may be talking about the same systems, but each has a very different regulatory framework. A cyber attack does not recognise these domains and what differentiates them.
Standards have a part to play in providing a framework to identifying and managing cyber risk, too. These are specific to the organisation’s needs and the services they provide. International standards such as ISO27000 give organisations a solid foundation and enable them to identify controls to their systems, the National Institute of Standards and Technology (NIST) provides a comprehensive eco-system of standards under a core framework. This is centred around an organisation’s ability to identify, protect, detect, respond and recover from a cyber attack.
Towards greater long-term flexibility
National Information Systems Regulation (NIS-R) is more applicable to those within the UK critical national infrastructure who are subject to the NIS Directive Cyber regulation and those managing cyber risks that may impact public safety. Even those who don’t currently fall within these categories may be driven towards a regulatory requirement by their evolving business strategy. Adopting NIS-R offers greater long-term flexibility should they head this way. Cyber resilience also offers a competitive advantage. Adopting standards, and implementing their controls, is a major step forward – but understanding maturity and setting goals enables an organisation to stand out from the competition and further attract business. This is especially relevant to high tech and critical infrastructure investments.
Streamlining IT processes and improving and automating systems will inevitably cut costs through the need for less administration – currently estimated to make up some 70% of the price of goods. Added to which, a secure data layer across Freeport operations will mean that, for example, a manufacturing business will know exactly where its components are, in near real time, and operate a much more efficient business. And this could prove another welcome side effect of Freeports, in their role as engines of innovation backed by data interfaces, data standards, and good cyber security.
Ensuring essential cyber resilience
So, protecting Freeports, as part of the UK’s national infrastructure, will be crucial. This activity should cover many aspects of a Freeport’s operations, from the more visible estate – such as precision-timed port gantry systems – to asset tracking and shipping manifests that are linked to tax payments. In this latter example, assets would move from one location to another – with payments demanded being based on gantry data. But undermine this process, and the trust in port operators’ ability to handle goods safely and securely – and therefore ensure correct charging – is severely eroded; inevitably attracting much interest from financial and insurance underwriters.
So, at the very least, there will need to be a service-level-type agreement across all Freeport operators, big and small, global conglomerates to local SMEs, that if they are connected to the internet, they must demonstrate they are protecting themselves. This is by taking the obvious measures of regular backups and antivirus software updates, but also by signing up to schemes such as Cyber Essentials, developed by the National Cyber Security Centre.
Other means could include all companies within the Freeport and beyond – including suppliers – having to apply a cyber security maturity model to their operations, to determine the level they are at, or taking an aggregated approach depending on business type and size.
Not implementing such recommendations as a matter of priority could come at a great cost: not only to Freeports’ overarching cyber resilience – but also in terms of protecting these important new parts of the UK’s infrastructure.
Seven steps to driving cyber resilience within Freeports
1. Ensure the business strategy addresses the challenges of cyber resilience
2. Demand that risk management processes include cyber resilience
3. Identify the impact that a cyber-attack might have on critical assets and
understand how that might happen
4. Build a culture of cyber awareness – it’s a collective responsibility
5. Ensure compliance to agreed standards and use best practice in hardening systems
6. Work with the supply chain to understand strengths and weaknesses.
7. Monitor networks, look for trends, and act on them.




